Worldwide security breaches have reached alarming levels, and producing secure embedded systems is more important than ever.
The cost of these breaches reached an all-time high in 2022, according to the Cost of a Data Breach Report 2022 report by IBM, hitting an average of $4.35 million per breach. Of those companies surveyed by IBM, 83% had already suffered a data breach before.
In a world where IoT embedded system usage is growing tremendously, building secure embedded systems is no longer a choice but an obligation.
Cyber insurance companies are starting to clamp down on insurance premiums because of the sheer number of attacks. The more secure embedded systems are, the more likely an insurance company is to offer a reasonable premium.
Building secure embedded systems in this cloud-connected world is an enormous challenge, however. Hackers get smarter and developers have enough on their plates trying to simply create devices that work.
So how can they ensure the development of secure embedded systems in the face of these obstacles?
In this article, we will dig into the subject of secure embedded systems, what options exist for building them, what challenges need to be overcome, and look at all the easy and robust ways to create secure embedded systems.
What is embedded system security?
Embedded system cyber security is a field dedicated to preventing the exploitation of embedded systems through malicious means. The field encompasses both hardware and software aspects.
Building secure embedded systems is an enormous subject that touches on a wide number of aspects. It is easy to get overwhelmed by all these aspects.
It's important to understand that cybersecurity is an entire field in itself and that nobody expects developers to suddenly stop developing and become cybersecurity specialists.
The same is true of device fleet managers. It would be expected that the developers of the IoT device management platform take care of security. One would not expect the fleet manager to become the organization's official pen tester (penetration tester) in addition to their job of doing Android fleet management.
That's why we recommend that developers focus on the Operating System and regular updates. When considering an embedded system and security aspects related to it, it's easiest to find an OS and hardware configuration that has a dedicated team of specialists behind it rather than trying to develop all the security elements yourself. Although nobody can guarantee an absolutely secure embedded operating system — new flaws are discovered all the time — lacking the proper update infrastructure and regular patches for newly discovered bugs will certainly guarantee poor security.
 Source: ESB Professional / Shutterstock
Source: ESB Professional / Shutterstock
Software security for embedded systems
Proper security for embedded systems requires robust software that is connected to an infrastructure that provides regular security patches so that potential security flaws are minimized. The other side of the coin is physical security.
Software security relates to how the embedded system software responds to malicious attempts to compromise it. Ideally, secure embedded systems would send an alert on detecting malicious behavior.
The software side of secure embedded systems also relates to firewalls, authentication, and most especially to the quality of the device's operating system.
There is also the aspect of physically secure embedded systems. This refers to such things as keeping embedded devices locked away, having surveillance cameras, and preventing unauthorized access to those devices.
The risk of physical access to a device cannot be understated. When coupled with software vulnerabilities such as an outdated and unpatched operating system, physical access can prove catastrophic.
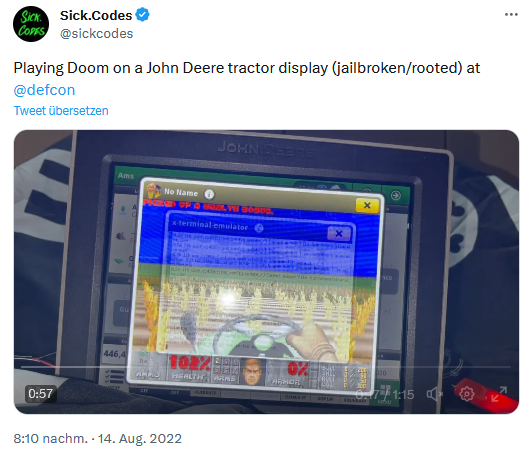
This was precisely the case in the "John Deere Jailbreak" demonstrated at 2022's Def Con — a hacker convention held in Las Vegas every year. After gaining physical access, multiple software vulnerabilities allowed the hacker to take full control of the device.
Source: Sick.Codes / Twitter / Screenshot
How secure are embedded systems?
An embedded system is as secure as the security of its firmware, operating system, and physical location combined. Limited physical access coupled with robust software is the only guarantee of creating secure embedded systems.
Embedded system security challenges
Are embedded systems secure if their software is out of date and unpatched? Absolutely not. And one of the first major challenges of security for embedded systems is finding an operating system that can be easily updated.
No software is perfect. And installing an operating system such as embedded Android on a device and then never updating it is a sure way to becoming a victim of a security breach. This is so important that IoT OTA updates (Internet of Things "Over-the-Air" updates) have now become mandated by European law.
To provide OTA firmware updates or just plain OTA updates to the operating system, it is necessary to have a device with an internet connection. So if you want to run Android on Raspberry Pi or on an x86 device, for example, be sure to select a device that has internet connectivity.
Whatever OS you install, it has to (a) be able to run/execute OTA and FOTA Updates ("Firmware Over the Air" updates), and (b) be connected to an infrastructure that provides these updates.
Sixty percent of all security breaches are in some way linked to unpatched vulnerabilities in software. The vulnerabilities affecting secure embedded systems could be in the firmware, operating system, or in an app.
Allowing such vulnerabilities to exist is often careless because many of those vulnerabilities are known about and there are often publicly available solutions to fix them.
Once you have an OS that can be updated over the air, and it is connected to a robust update infrastructure, the next step becomes managing these updates on a browser-based UI so that these updates can be pushed to the device easily.
If the browser-based UI allows for full Mobile Device Management (MDM), then you will receive other benefits of MDM totally aside from just the OTA Updates. For example, using MDM, you can carry out fully-fledged Raspberry Pi fleet management, or management of any other fleet of devices, such as x86 and Radxa ROCK devices. This also greatly enhances the security for embedded systems because it gives the fleet manager full control of these devices and their security settings.
Other secure embedded systems challenges
Another embedded system security issue is a lack of developer awareness. Because embedded systems are so varied, many developers aren't completely familiar with the best practices to secure embedded systems. Embedded devices are also generally far more complex than other devices.
Developers who are not experts in developing these devices must balance their lack of knowledge with performance issues and writing safe code.
It is unfair on some developers to expect them to know everything about security for embedded systems. It is a realm that is best left to experts, and especially to the developers of the underlying operating system and update infrastructure.
If you have teamed up with a company offering a robust underlying operating system that is regularly updated, then you have already laid the foundation in the field of security for embedded systems.
Third-party components
 Using third-party components can greatly complicate security for embedded systems. You cannot vouch for any third-party code used in your embedded device and so must hope that the component was created properly. This is why some companies try to implement security for embedded systems with their own homegrown OS. But achieving proper security standards that way is virtually impossible.
Using third-party components can greatly complicate security for embedded systems. You cannot vouch for any third-party code used in your embedded device and so must hope that the component was created properly. This is why some companies try to implement security for embedded systems with their own homegrown OS. But achieving proper security standards that way is virtually impossible.
Purchasing a custom operating system made for your specific embedded hardware poses additional risks. Providers of these custom OSes usually only include the creation of an Android operating system image, but not long-term update services for newer software versions — not to mention integrating the latest security patches, fixing software bugs, and rolling out improved services.
You're far better off going with a company that works dedicatedly with one particular OS, allows that OS to be updated, and that has the infrastructure behind it to carry out those updates.
No standardization
Implementations of security for embedded systems are not standard from one device to the other. The great variance in embedded devices means that each one will have a slightly different setup.
But although the details might be different, the major steps remain the same when implementing security for embedded systems, regardless of the device being used:
- Have a secure and regularly updated operating system.
- Link the device up with a strong OTA infrastructure, so those updates can happen without human intervention.
- Ideally, manage the device through an MDM so that other security aspects can be managed remotely (such as password policies and other security-sensitive settings).
Out-of-date software and apps
We touched on this earlier, but it merits its own section because of its importance. Secure embedded systems must be updated. There simply is no way around it.
Knowing this, the question then becomes How to do it?
Through the MDM tools we previously mentioned, everything on the device can be updated, not only the operating system and firmware but also individual apps that might have security flaws.
Direct connection to the internet
If a device has a direct connection to the internet, bypassing firewalls and other corporate protections, its security vulnerability is increased.
What are the benefits of secure embedded systems?
Embedded system security vulnerabilities lead to a degradation in trust between you and your customers. And, worse, they can lead to severe financial penalties and even damaged lives as a result of data breaches.
Although the challenges of security for embedded systems might be overwhelming, the benefits certainly make it worth it.
Here are the primary benefits of creating secure embedded systems:
Larger access to markets
Certain sectors, such as the health and government sectors, require extremely hardened secure embedded systems. Failure to provide secure embedded systems that match their standards will completely block entry into these markets.
The reason for this is the high-risk factor for these industries. A single health record can sell for several hundred dollars on the black market because it can be used to defraud insurance companies of many thousands of dollars. This makes the healthcare industry a prime target for hackers who are looking for weaknesses in security for embedded systems.
Government targets are likewise high-value for political motivations.
Compliance
 Although IoT regulations are few, the regulatory environment is always evolving. It's good business practice to foresee potential regulatory requirements and account for them.
Although IoT regulations are few, the regulatory environment is always evolving. It's good business practice to foresee potential regulatory requirements and account for them.
For example, a few years ago, the EU and Germany enacted a law that requires software to be regularly updated. Companies that had created secure embedded systems by enabling OTA updates were prepared for these laws and didn't have to do anything to comply.
But companies that had not created secure embedded systems in this way were given a time limit in which to comply. This can lead to large unexpected costs.
Confidence from customers = higher revenue
Implementing security for embedded systems increases customer confidence, which in itself can increase revenue.
Trust has both a significant and direct impact on revenue. Those companies that have a high trust level are 2.5 times more likely to be high-revenue organizations. And, according to research published in Harvard Business Review, trusted companies outperform their peers by up to four times.
Conversely, data breaches reduce trust in an organization by 65%, according to a study by Centrify.
So security for embedded systems is vital to staying afloat in this world of ever-growing cyberattacks and cyber threats.
Competitive advantage
Because the IoT landscape is largely unregulated, companies that focus on secure embedded systems will automatically have a competitive advantage over companies that don't.
Integrated security
Unlike traditional computers, secure embedded systems must typically be secured primarily at the firmware level. This means that security is virtually baked into the device itself.
This has the advantage of making the embedded device potentially even more secure than its traditional counterparts.
The only other requirement is that the firmware can be easily updated remotely.
How to secure embedded systems?
The way to secure embedded systems is to ensure (a) the embedded operating system is robust, (b) the device receives secure updates, and (c) that the OS is actively maintained. There are many other details, but these are the most important.
Actionable ways to secure embedded systems
There's a principle in developing security systems called the "CIA Triad." It is also sometimes called the "AIC Triad" to avoid confusion with the Central Intelligence Agency of the United States.
 The CIA Triad stands for Confidentiality, Integrity, and Availability. (Or Availability, Integrity, and Confidentiality in the case of the AIC version.)
The CIA Triad stands for Confidentiality, Integrity, and Availability. (Or Availability, Integrity, and Confidentiality in the case of the AIC version.)
When considering security for embedded systems, one must ensure that each of these points is addressed. Broadly speaking, if the device's data remains confidential (lack of data breaches), the device's integrity is not compromised in any way, and the device remains available, then one has fulfilled the requirements for creating secure embedded systems.
A secure operating system, secure updates, and active maintenance ensure the CIA Triad is fully implemented.
Secure operating system
Above all else, the operating system you use must be secure and patched. Open-source OSes are fine but can have their limitations if they do not have a huge community behind them. Android is an excellent choice as an operating system for improving security for embedded systems because there is massive community support for it.
But Android won't work on most embedded devices out of the box and so you would need a version of Android that has been specifically designed to work on these devices, and which is actively supported.
Secure updates
Even if the operating system you choose is robust, you will need regular and secure updates to that operating system to create fully secure embedded systems. New bugs are found all the time, and cybercriminals get better at what they do, so regular updates are vital to ensure you have secure embedded systems.
Maintenance
If you have a strong operating system that is regularly updated, most of your team's own maintenance tasks will already be taken care of.
Security measures for embedded systems
A number of security tools for embedded operating systems exist to test embedded system IoT security. The most secure embedded system will be tested regularly with these tools, and the hardening of security for embedded systems is often done in combination with these tools.
In addition to the tools, the other important measure is securing the network the device is on.
Embedded systems design secure network
The security of your network directly relates to developing secure embedded systems. If your embedded devices are network-connected but not physically accessible, then the way hackers can gain access to them is through your network.
So any tools developed for testing network security are 100% valid in improving security for embedded systems.
Also, the company providing updates must ensure that they are transferred through a secure connection and a hardened network.
The growing popularity of Android in secure embedded systems
Android is becoming increasingly popular in the IoT space. There are several benefits to choosing Android for IoT devices, including:
- Familiar user interface
- Easy updatability (provided the infrastructure exists within the embedded Android OS)
- Huge community support
- Plenty of developers
- Actively maintained
- Proven OS
- Designed for ARM architecture and smaller devices
- Excellent touch-screen support
Like all OSes, unpatched versions can still lead to attacks, as occurred in some older versions of Android. If a company does not have the update infrastructure in place to provide OTA updates, this poses a huge risk to creating fully secure embedded systems.
Furthermore, in-depth knowledge of Linux is required if you plan on modifying stock Android to work on embedded devices.
To ensure fully secure embedded systems, it is best to go with an Android version that has already been modified to work on embedded devices, and which connects with a reliable OTA infrastructure, such as emteria.OS.
Implement secure embedded systems with emteria
Emteria provides a fully-fledged Android operating system that comes packaged with OTA functionality, remote management, and the necessary update infrastructure to keep it up to date.
Through emteria's Device Hub, devices can be updated and modified remotely. Their settings and policies can also be changed to ensure that these devices remain secure.
Emteria.OS is regularly updated and has a strong team behind it. It is an enterprise-ready solution that takes most of the complexity out of creating secure embedded systems.
Build unique Android products, keep them secure
See why emteria is the chosen Android™ customization & management platform for product builders — build secure Android products and keep them updated with OTA updates.